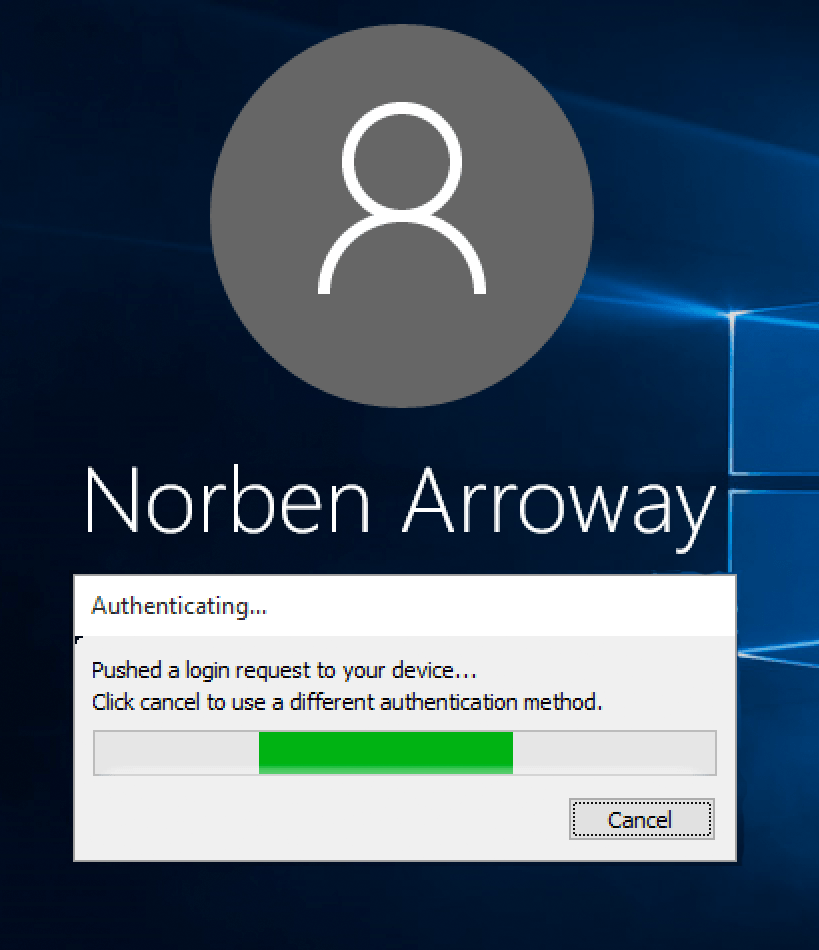
Let’s say you want to protect your server’s RDP sessions from attacks. What are the most basic steps? Disable the Administrator account, change the RDP port, enable NLA, and use a complex password. Of course. But those are all old strategies. What’s the best way nowadays to protect your authentication? Two-factor! I decided to give Duo a try.
Duo is one of the leading security companies in regards to RDP Two-Factor right now. One thing that I loved about them almost immediately is that all their documentation is publicly available, and easy to follow. I literally got my two-factor set up in about 15 minutes or less:
- Sign up for a Duo account.
- Log in to the Duo Admin Panel and navigate to Applications.
- Click Protect an Application and locate Microsoft RDP in the applications list. Click Protect this Application to get your integration key, secret key, and API hostname.
- Download the Duo Authentication for Windows Logon Installer Package.
- Install the Duo Authentication application on your server using your integration key, secret key, and API hostname.
- Create a Duo Account user on the website to allow for authentication.
Their web application is kind of cluttered, and I don’t like that I have to use a separate Duo iOS app instead of Google Authenticator, but the two-factor works great. When I try to RDP into my server, I am prompted to tap “accept” in my Duo iOS app, and then I’m in!